The Discovery of the DeepSeek Data Leak
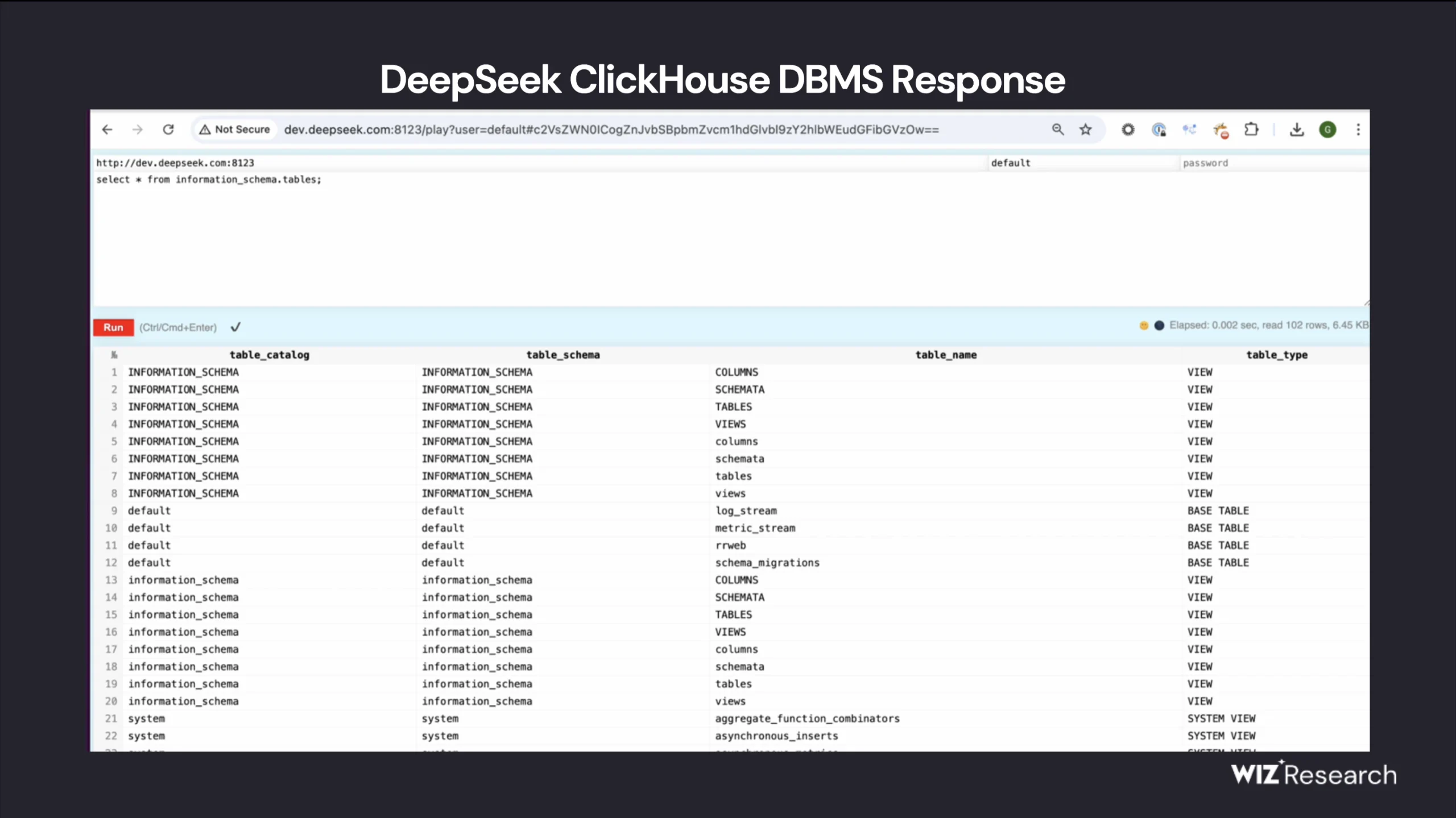
Security researchers at Wiz identified an unauthenticated ClickHouse database accessible from:
oauth2callback.deepseek.com:9000dev.deepseek.com:9000
This database, completely open to the internet, contained highly sensitive information, including logs of user interactions, API keys, and backend configurations.
(Source: Wiz Research)
By using ClickHouse’s HTTP interface, researchers executed queries via a browser, extracting system logs, API secrets, and internal server details.
Security Risks and Consequences
The leak posed multiple security threats:
1. User Privacy Breach
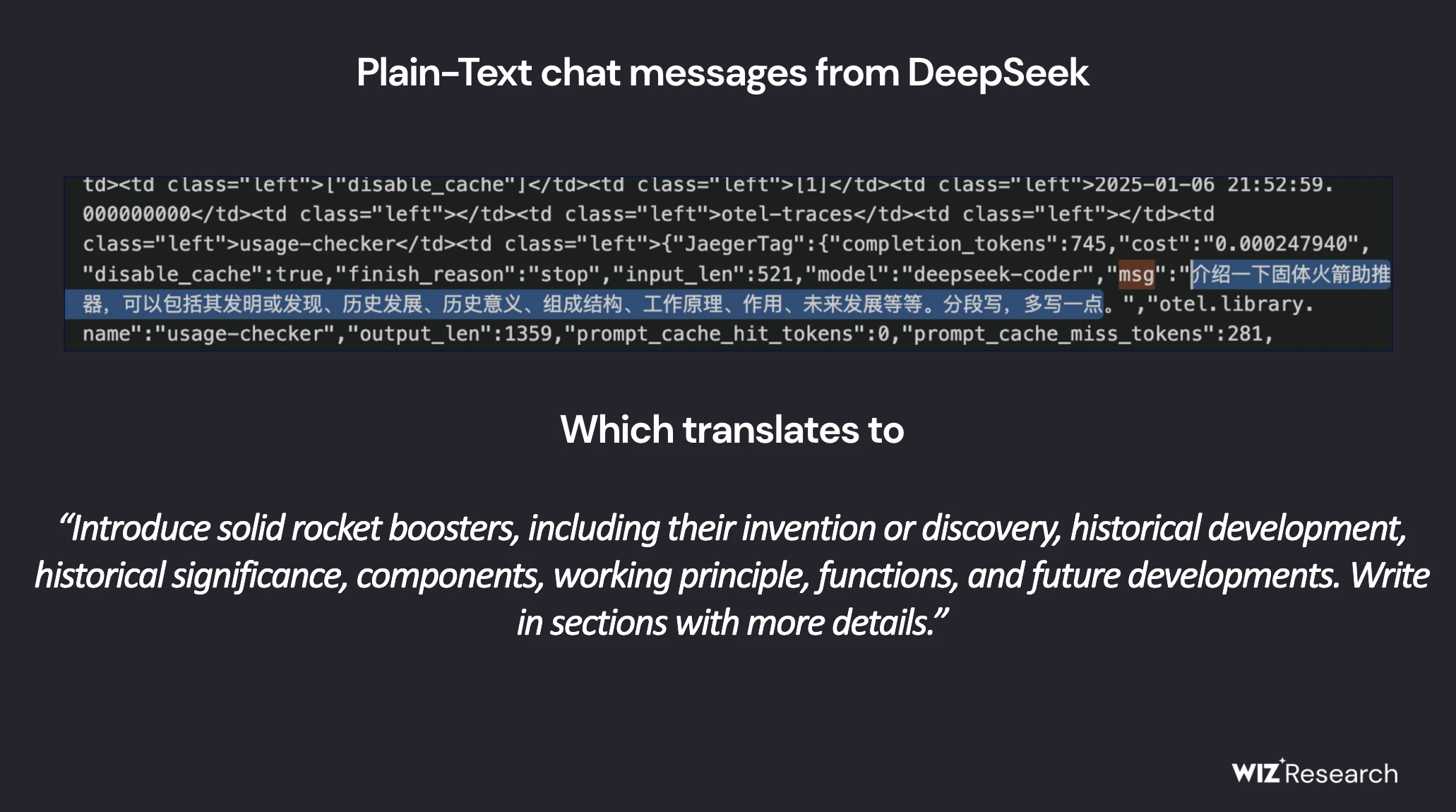
The log entries contained plain-text chat histories, potentially exposing private conversations and user data.
(Source: Wiz Research)
2. API Key Leakage
Attackers could use exposed API keys to access DeepSeek’s backend, impersonate users, or manipulate AI outputs.
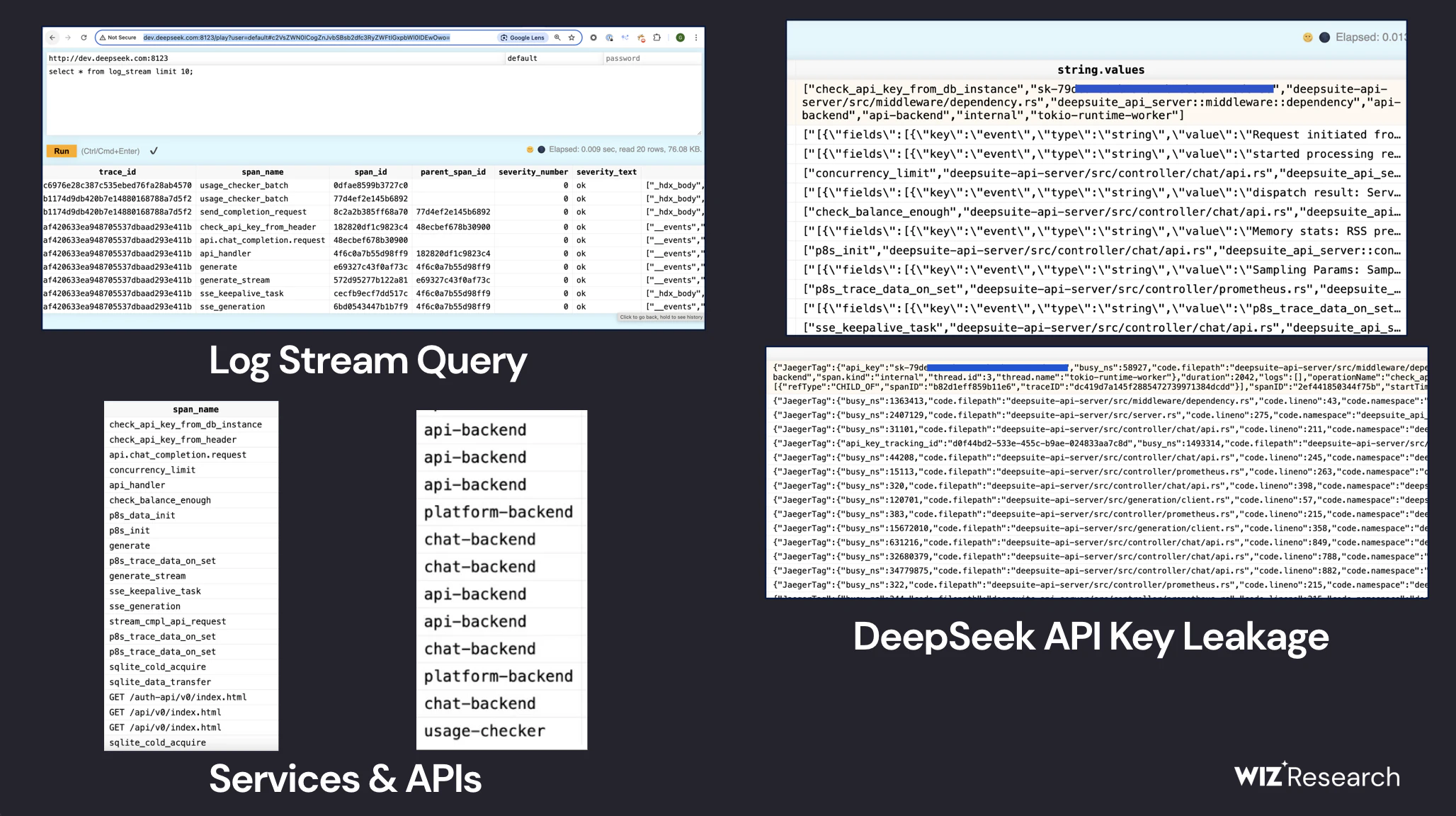
(Source: Wiz Research)
3. Infrastructure Vulnerabilities
The exposure allowed privilege escalation and the ability to execute queries directly on DeepSeek’s database.
(Source: Wiz Research)
Technical Details of the Exposure
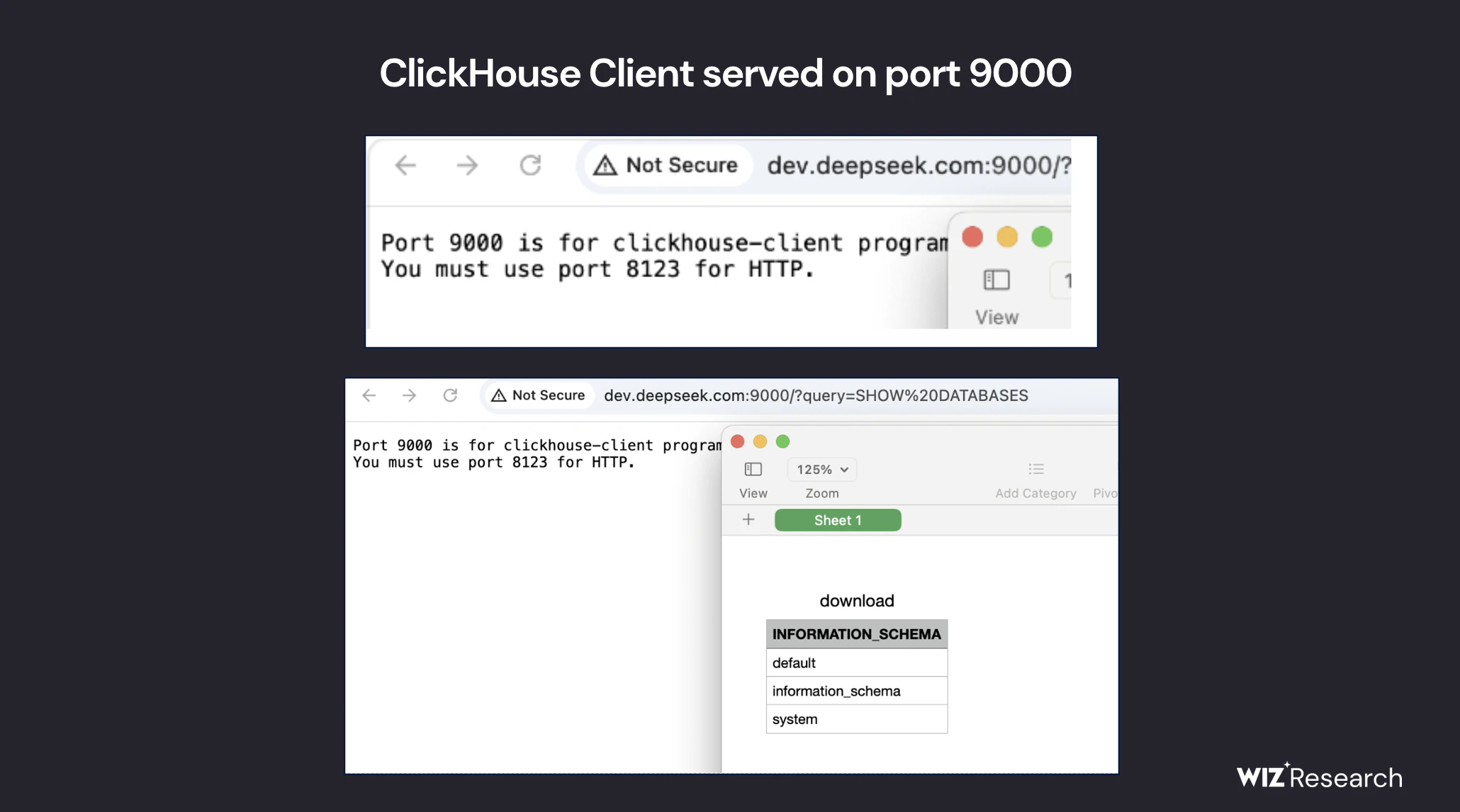
Upon further inspection, researchers found that DeepSeek’s ClickHouse server was exposed via ports 8123 and 9000, making it publicly accessible without authentication.
(Source: Wiz Research)
They ran a simple SQL command (SHOW TABLES;), which listed multiple internal datasets, including log streams and operational metadata.
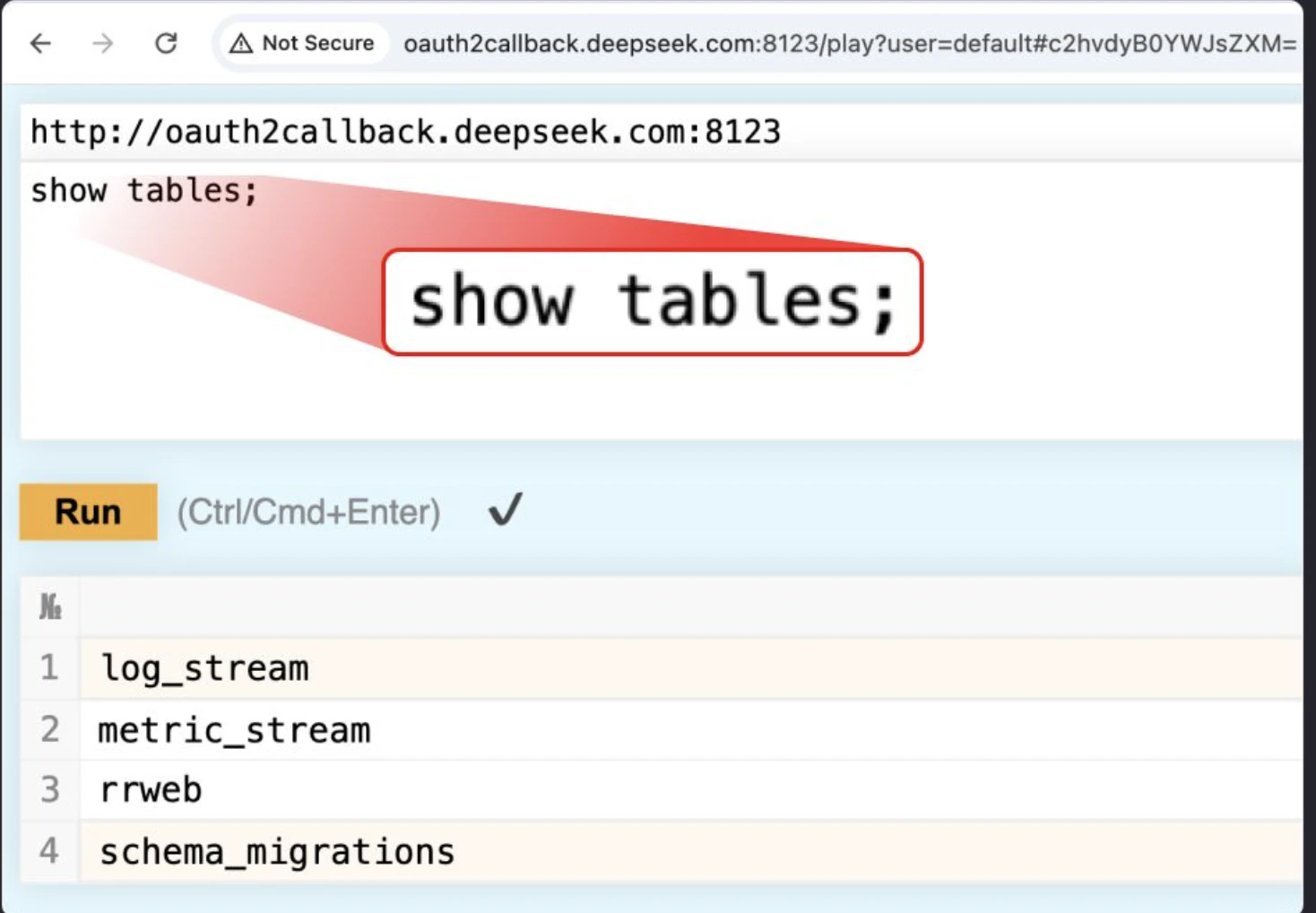
(Source: Wiz Research)
DeepSeek’s Response
Upon notification by Wiz Research, DeepSeek immediately secured the database, preventing further unauthorized access. However, no official statement has been made regarding whether any unauthorized breaches occurred before the fix.
Lessons for the AI Industry
This incident serves as a critical reminder that AI startups must prioritize security to prevent data leaks and infrastructure vulnerabilities.
Key Takeaways:
✅ Restrict Database Access: Use authentication and firewall rules to limit exposure.
✅ Encrypt Sensitive Data: Store API keys and chat histories securely.
✅ Monitor Infrastructure: Implement real-time threat detection.
✅ Regular Security Audits: Conduct penetration testing to prevent accidental exposure.
Final Thoughts
AI companies are expanding faster than security measures can keep up. As AI becomes critical to businesses, ensuring secure data management practices is more important than ever.
This DeepSeek exposure highlights the real dangers of misconfigured AI infrastructure. Moving forward, companies must prioritize security to avoid similar breaches.